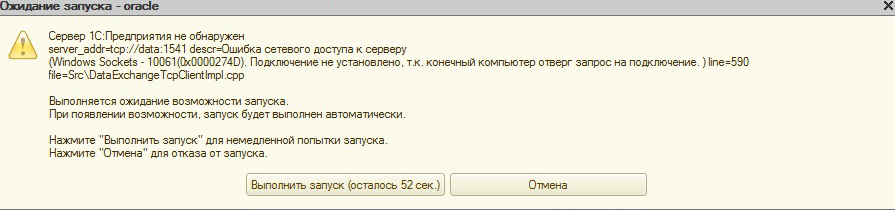
Server 1c enterprise not detected server addr. Correct - start the server. Error Subd: database is not suitable for use.
Errors that reveal themselves when working with software products often make it impossible to use them. And the lack of special knowledge for understanding the operation algorithms also generates the impossibility of diagnosing and correcting the failures that occur. In this article, let's look at the problem “1C: Enterprise Server not found, how to fix the launch of the agent-server?”.
You had better go through the following checklist to correct the problem “refused connection”. Check whether the name of the target machine. In this situation, this is possible because of an invalid client request. But do not worry, because if this happens to you, or it happens to you, in just 5 steps you can solve it.
Now we will begin to solve this error, but we'll see, because it is important to correctly install and enter all the numbers. There we go! The procedure is simple, it fills the fields only with these numbers. But if you have any doubts, feel free to leave a comment. Did this tutorial help? Is the bug fixed?
There are several ways to solve the problem in the work of 1C.
The errors that occur have a different background, they can be sorted by level of occurrence:
- Incorrect writing of codes by the developers of one-eski itself;
- Errors made by programmers who modify (change) the product in relation to the requirements (tasks) of a particular user;
- Failures caused by errors in the work of the cache, most often confusing programmers;
As for the error “1C: Enterprise server is not detected”, it is unrealistic to attribute to one of these, since such a notification is an indication to the user that a certain necessary action was not taken for the program to work.
Principle of minimum privilege
You should have some familiarity with operating system installations and the command line. To fully understand the concepts of this lesson, you had to follow the accompanying textbook ".". Internet connection is also required to download certain software packages used in the tutorial. A truly secure network ensures that the principle of minimum privilege applies to the enterprise, and not just to servers. The functions performed by servers and desktops also determine how the operating system should be protected, the computer.
Correct - start the server
So - the situation, which is devoted to this publication occurs in the case when the agent-server service is either disabled or stopped. Note that, as a rule, the reasons for this remain unclear (who is recognized).
The desktop can be an attractive place for a script for children whose attacks are always hampered by modern software and malware scanners, but a data center with user accounts or credit card information is a much more attractive target for a qualified hacker. in an environment that was not protected.
Several options for finding errors and solutions
Protecting a server is very different from protecting a desktop computer for various reasons. The default is the desktop operating system, which provides the user with an environment that can start automatically. Desktop operating systems are sold with the premise that they require minimal configuration and are loaded with as many applications as possible that can be started and run by the user. Conversely, the server operating system must follow the principle of minimum privilege, which states that to perform tasks for which it is responsible, there must be only services, software and permissions.
This service is launched in two ways - either as an application or as a service. Let's see how to do it in both cases:
As an application
To run it as an application, run the command:
At that, the port, port ranges, level and directory are specified (in their settings). If these parameters are not specified, their values will be set by the program “by default”.
Revision of unchangeable security laws
There are two versions of these laws: one for users and one for system administrators. Over the years, these laws have been reviewed and ignored by people in the security market segment. Despite some negative reviews, 10 laws for administrators can serve as an excellent basis for protecting any system if it is applied correctly.
Error subd: database is not suitable for use
First, the following law applies to general safety rules: Security only works if the secure method is also the easiest way. This is the most important law for any system administrator. The best example is associated with passwords.
The 1C: Enterprise server bundle and PostgreSQL are the second most popular among 1C installations and the most used solution on the Linux platform. Unlike Windows-based and MSSQL deployments, where it is difficult to make it work, Linux-based deployments pose many pitfalls for an inexperienced administrator. It often happens that everything seems to be done correctly, but the error follows the error. Today we look at the most typical of them.
Correct - start the server
Requiring users to remember a password consisting of 15 characters in capital letters, lower case letters, numbers and symbols should ask a high percentage of users to enter their password in the post-it and place it on their monitor. The four laws of Kalpa apply directly to the material described in this lesson.
Planning Server Installation
If you are not aware of the latest security patches, your network will not be long. As a system administrator, you need to make sure your system is up to date. Safety is not to avoid risks; This is due to risk management. Facts happen. There may be a malware epidemic, or your website may be attacked. Or something completely out of your control can happen, like a natural disaster. At one time or another, the security of your system will be checked. Make sure that you have done everything possible to protect your system and eliminate the threat so that your server and resources are available to users who rely on them. Technology is not a tool that can cure all diseases. If there is a law that must be known by all those who work with technology, that's all. Simply throwing more technology into a security issue will not solve it.
- Hackers discover vulnerabilities every day.
- But this leads to a difference between protecting the desktop and protecting the server.
- Surveillance is what protects your system.
general information
Before starting to look for installation errors and, in general, it would be nice to refresh the implementation of the server version of 1C: Enterprise to refresh the view on how it works:
In small implementations, the 1C server and the DBMS server are usually combined on the same physical server, which slightly narrows the range of possible errors. In our case, the situation will be considered when the servers are separated by different machines. In our test lab, we deployed the following scheme:
The only applications and services that they should allow to run on their servers are those that are necessary for the task that the server must perform. No additional elements should be installed for two reasons. Installing additional software or performing additional services means that there is another door that needs to be blocked. Its simple existence on the server will give the hacker another way to access his system. Similarly, any other software installed on this server must be updated, repaired, and monitored to ensure that it does not represent a vulnerability that a hacker can exploit. Installing additional software on the server means that someone will be tempted to use such a server for something that is not related to its intended use. Using the server for other tasks not only removes resources from your primary task, but also provides the server with threats that are unlikely to affect it without software installed on it. Among other things, you must decide whether to install a graphical user interface.
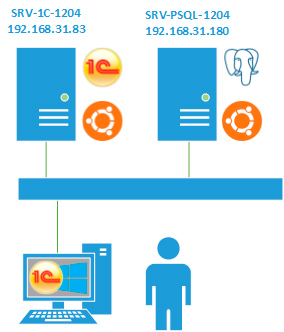 We have two servers running Ubuntu 12.04 x64, one of them has a 1C: Enterprise version 8.3 server, another PostgreSQL 9.04 from Ethersoft, and a client running Windows. We remind you that the client is working only with 1C server, which, in turn, generates the necessary requests to the database server. No requests from the client to the database management server not happening.
We have two servers running Ubuntu 12.04 x64, one of them has a 1C: Enterprise version 8.3 server, another PostgreSQL 9.04 from Ethersoft, and a client running Windows. We remind you that the client is working only with 1C server, which, in turn, generates the necessary requests to the database server. No requests from the client to the database management server not happening.
Security through obscurity
This side also emphasizes that commands can be quickly entered on the command line, without the need to browse menus and folders when performing a task. Once you are logged in, you must gain access to the command line. When the installation of any of the packages is complete, it is still on the command line. You can always return to the original.
Users on the unlock list
Now you need to find the part of the file in which the port number is configured. Once you place it, you can change it to an arbitrary number. There are over a thousand doors; Select something at the top of the scale, but the number you remember. Remember, experienced hackers know what people think. This process is known as an unlock list.
IMPORTANT: user "postgres" did not authenticate (Ident)

This error occurs when server servers are spread across different PCs due to incorrectly configured authentication on the local network. To eliminate open /var/lib/pgsql/data/pg_hba.conf, find the line:
Instead of a username, replace the usernames of your list. . You can deny access to your server through a firewall.
- You will see the message "The firewall is started and turned on at system startup."
- Now you can create rules for your firewall.
You can also allow or deny traffic in accordance with the protocol used. You will see a list of rules that you have already created for your firewall. If you see the rule you want to delete, enter. Security circles on computers say that the only way to truly protect a computer is to completely turn it off and lock it in the drawer. Not so simple, but the main message is that if a hacker really wants to hack the system, he will most likely find a way.
Host all all 192.168.31.0/24 ident
and bring it to mind:
Host all all 192.168.31.0/24 md5
where 192.168.31.0/24 - range of your local network. If there is no such line, it should be created in the section IPv4 local connections.
Database server not detected
could not translate host name "NAME" to address: Temporary failure in name resolution
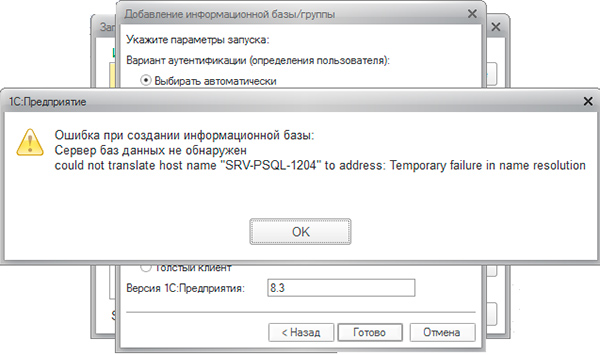 At first glance, the error is clear: the client cannot resolve the name of the DBMS server, a typical error for small networks where there is no local DNS server. As a solution, add an entry to the file. hosts on the client that does not give any result ...
At first glance, the error is clear: the client cannot resolve the name of the DBMS server, a typical error for small networks where there is no local DNS server. As a solution, add an entry to the file. hosts on the client that does not give any result ...
After completing the intrusion prevention steps, you need to set up a monitoring system to determine whether an attack has been installed on your server. Then, if you are warned about the attack, it is best to prepare for it in advance. The following sections describe the steps to install and configure two programs that help detect intrusions.
An error occurred while performing an information base operation server_addr = NAME descr = 11001 (0x00002AF9): This host is unknown
It then reports any anomalies on this baseline via an email or magazine alert. In fact, if the system binaries have been changed, you will know about it. If a legitimate installation causes such a change, there are no problems.
And now we recall what was said a little earlier. The client of the DBMS server is 1C server, but not the client PC, so the record must be added on the 1C: Enterprise server to the file / etc / hosts on the Linux platform or in on the Windows platform.
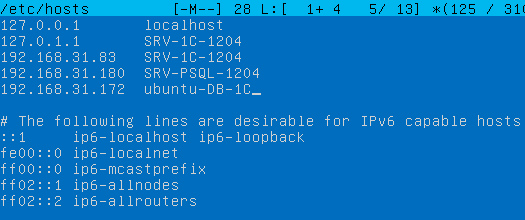
A similar error will occur if you forget to add Type A Record for the DBMS server on the local DNS server.
But if the binaries are changed as a result of installing a trojan or rootkit, it has a starting point for searching for attacks and fixing problems. You can start the database by typing. This baseline will be used to check for critical file changes. If such a change is detected, a warning will be sent. You can perform integrity checks at any time by following these steps.
You will receive a report that will be saved in the report catalog. . This program requires an email server running on your network to send logs by email. To email the logs to yourself, enter. Clicking sends a copy of the report to the specified email address.
Error while performing information base operation
server_addr = NAME descr = 11001 (0x00002AF9): This host is unknown.
![]() Like the last one, this error is due to the client's incorrect resolution of the server name. This time it is the client PC. As a solution, add to the file / etc / hosts on the linux platform or in C: \\ Windows \\ System32 \\ drivers \\ etc \\ hosts on the Windows platform, the following entry:
Like the last one, this error is due to the client's incorrect resolution of the server name. This time it is the client PC. As a solution, add to the file / etc / hosts on the linux platform or in C: \\ Windows \\ System32 \\ drivers \\ etc \\ hosts on the Windows platform, the following entry:
You can organize users into groups to simplify administration, but you also need to grant access to files and folders through permissions. No common “user of authority” gives users access to anything on a computer or network.
The user level defines the user who created the file or directory, the group level determines the group in which the user is located, and the other level for any user outside the user group. File permissions - read, write and execute. . You can apply a numeric value to each resolution. Thus, if the user can read, write, and execute, you include the corresponding numbers 4, 2, and 1 for the total of the following group permissions. For example, other members of a user group may be able to read and execute, but not write.
192.168.31.83SRV-1C-1204
where you specify the address and name of your 1C: Enterprise server. If using a local DNS, add A-record for 1C server.
DBMS Error: DATABASE Not Usable
 A much more serious error, which indicates that you installed the PostgreSQL version incompatible with 1C: Enterprise or made gross errors during the installation, for example, did not install all the necessary dependencies, in particular the library libICU.
A much more serious error, which indicates that you installed the PostgreSQL version incompatible with 1C: Enterprise or made gross errors during the installation, for example, did not install all the necessary dependencies, in particular the library libICU.
If you have sufficient experience in administering Linux systems, you can try to install the necessary libraries and reinitialize the database cluster. Otherwise, it is better to reinstall PostgreSQL, not forgetting to delete the contents of the folder. / var / lib / pgsql.
Also, this error may occur when using assemblies 9.1.xand 9.2.x [email protected] , see below for details.
DBMS Error:
ERROR: could not load library "/usr/lib/x86_64-linux-gnu/postgresql/fasttrun.so"
 Quite a specific build error 9.1.xand 9.2.x [email protected]
may also result in a previous error. The reason lies in the uncorrected error in the fasttrun.so library. Solution - roll back to build 9.0.x [email protected]
.
Quite a specific build error 9.1.xand 9.2.x [email protected]
may also result in a previous error. The reason lies in the uncorrected error in the fasttrun.so library. Solution - roll back to build 9.0.x [email protected]
.
DBMS Error
ERROR: type "mvarchar" does not exist at character 31
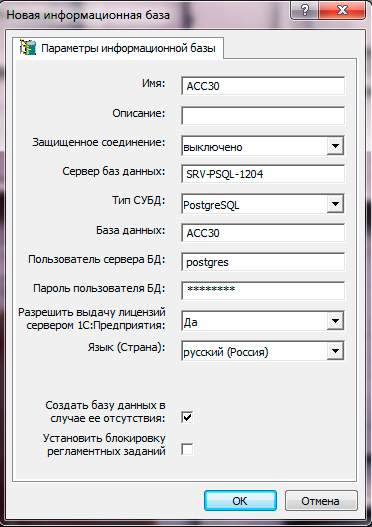
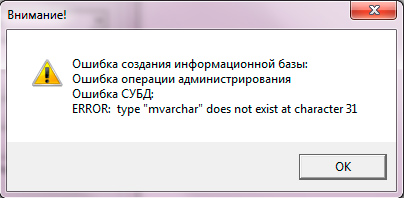 It occurs if the database was created without the help of the 1C: Enterprise system. Remember, to work with 1C database should be created only using the tools of the 1C platform: via the console
It occurs if the database was created without the help of the 1C: Enterprise system. Remember, to work with 1C database should be created only using the tools of the 1C platform: via the console
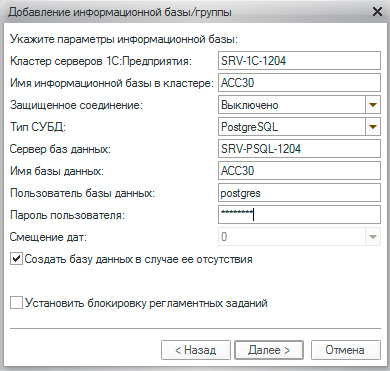
or through the launcher 1C.
Database server not detected
IMPORTANT: user "postgres" did not authenticate (password)
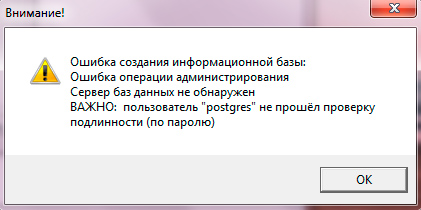 Very simple mistake. The password for the postgres DBMS superuser is incorrect. There are two possible solutions: remember the password or change it. In the second case, you will need to change the password in the properties of all existing information databases through the snap-in. Administration of 1C Enterprise servers.
Very simple mistake. The password for the postgres DBMS superuser is incorrect. There are two possible solutions: remember the password or change it. In the second case, you will need to change the password in the properties of all existing information databases through the snap-in. Administration of 1C Enterprise servers.
Database server not detected
FATAL: database "NAME" does not exist
 Another very simple mistake. Its meaning is that the specified database does not exist. Most often arises because of an error in specifying the name of the database. It should be remembered that the 1C information base in the cluster and the database of the DBMS are two different entities and may have different names. Also, remember that Linux systems are case sensitive and for them unf83 and UNF83 two different names.
Another very simple mistake. Its meaning is that the specified database does not exist. Most often arises because of an error in specifying the name of the database. It should be remembered that the 1C information base in the cluster and the database of the DBMS are two different entities and may have different names. Also, remember that Linux systems are case sensitive and for them unf83 and UNF83 two different names.