What are firewalls really? Firewall
A firewall is a software-hardware or software element that controls network traffic on the basis of specified parameters and, if necessary, filters it. It may also be called a firewall or firewall.
Firewall Assignment
Firewall is used to protect individual network segments or hosts from possible unauthorized entry through software vulnerabilities installed on PCs or network protocols. The job of the network crane is to compare the characteristics of the traffic passing through it with the patterns of the already known malicious code.
The most common firewall is installed on the perimeter of the local network, where it performs the protection of internal nodes. However, attacks can be initiated from the inside, so when attacking a server on the same network, the firewall will not perceive this as a threat. This was the reason why firewalls began to be installed not only at the edge of the network, but also between its segments, which significantly increases the network security level.
History of creation
Firewalls begin their history from the end of the eighties of the last century, when the Internet has not yet become an everyday thing for most people. Their function was performed by routers that performed traffic analysis based on data from the network layer protocol. Then, with the development of network technologies, these devices were able to use data already transport level. In fact, the router is the world's first software firewall implementation.
Software firewalls emerged much later. So, Netfilter / iptables, a firewall for Linux, was created only in 1998. This is due to the fact that earlier the function of the firewall was performed, and very successfully, by antivirus programs, but since the end of the 90s viruses have become more complex, and the appearance of a firewall has become necessary.
Traffic filtering
Traffic is filtered based on the rules specified - ruleset. In essence, a firewall is a sequence of analyzing and processed traffic filters according to this package of configurations. Each filter has its own purpose; Moreover, the sequence of rules can significantly affect the performance of the screen. For example, when analyzing traffic, most firewalls consistently compare it with known patterns from the list — obviously, the most popular types should be located as high as possible.
Principles on which the processing of incoming traffic, there are two. According to the first, any data packets, except for prohibited ones, are allowed, so if it does not fall under any restriction from the list of configurations, it is passed on. According to the second principle, only those data that are not prohibited are allowed - this method provides the highest degree of security, but significantly loads the administrator.
The firewall performs two functions: deny, prohibiting data - and allow - allowing further transmission of the packet. Some firewalls are also able to perform a reject operation - to prohibit traffic, but inform the sender about the unavailability of the service, which does not happen when the deny operation is performed, thus providing greater host protection.
Firewall Types
Most often, firewalls are classified according to the supported level of the OSI network model. There are:
- Managed Switches;
- Packet filters;
- Session level gateways;
- Application Level Intermediaries;
- Inspectors state.
Managed Switches
Often, they are considered to be a class of firewalls, but they perform their function at the data link layer, therefore, they are not able to handle external traffic.
Some manufacturers (ZyXEL, Cisco) have added to their product the ability to process data based on the MAC addresses contained in the frame headers. However, even this method does not always bring the expected result, as the MAC address can be easily changed using special programs. In this regard, in our days, switches are often focused on other indicators, namely, VLAN ID.
VLANs allow you to organize groups of hosts, in which data is completely isolated from external network servers.
Within corporate networks, managed switches can be a very effective and relatively inexpensive solution. Their main disadvantage is the inability to process the protocols of higher levels.
Packet filters
Packet filters are used at the network level, monitoring traffic based on data from the packet header. Often they are also capable of handling protocol headers and higher level transport (UDP, TCP). Packet filters have become the very first firewalls, and remain the most popular today. When receiving incoming traffic, such data is analyzed as: IP of the receiver and sender, type of protocol, ports of the receiver and source, service headers of the network and transport protocols.
The vulnerability of packet filters is that they can skip malicious code if it is divided into segments: packages present themselves as part of other, allowed content. The solution to this problem is to block fragmented data, some screens can also defragment them on their own gateway - before sending to the main network node. However, even in this case, the firewall may become a victim of a DDos attack.
Packet filters are implemented as OS components, border routers, or personal firewalls.
Packet filters have a high packet analysis rate, perform their functions perfectly at the boundaries with networks of low confidence. However, they are unable to analyze high levels of protocols and can easily be victims of attacks that fake a network address.
Session Level Gateways
The use of a firewall eliminates the direct interaction of external servers with a host — in this case, it plays the role of an intermediary, called a proxy. It checks every incoming packet, not missing those that do not belong to the previously established connection. Those packets that pretend to be packets of an already completed connection are discarded.
The session-level gateway is the only link between the external and internal networks. Thus, it becomes difficult to determine the network topology that the session-level gateway protects, which greatly increases its security against DoS attacks.
Nevertheless, even this solution has a significant disadvantage: due to the lack of ability to check the content of the data field, a hacker can transfer Trojans relatively easily to the protected network.
Application Level Intermediaries
Like session-level gateways, application-level firewalls mediate between two nodes, but they have a significant advantage — the ability to analyze the context of the transmitted data. A firewall of this type can identify and block unwanted and non-existent sequences of commands (this often means a DOS attack), and also prohibit some of them in general.
Application level mediators determine the type of information transmitted - a striking example is postal services that prohibit the transfer of executable files. In addition, they can authenticate the user, the SSL certificates have a signature from a specific center.
The main disadvantage of this type of firewall is a long packet analysis, which requires time-consuming. In addition, application-level intermediaries do not have auto-connection to support new protocols and network applications.
State inspectors
The creators of the state inspectors set a goal to bring together the advantages of each of the above types of firewalls, thus obtaining a firewall capable of processing traffic at both the network and application levels.
State inspectors monitor:
- all sessions - based on the state table,
- all transmitted data packets - based on a given table of rules,
- all applications based on developed intermediaries.
Filtering of the status inspector's traffic occurs in the same way as when using session-level gateways, due to which its performance is much higher than that of application-level intermediaries. The state inspectors have a convenient and understandable interface, easy setup, and extensive extensibility.
Implementation of firewalls
Firewalls (Firewall) can be either software and hardware, for software. The former can be implemented as a separate module in a router or switch, or as a special device.
Most often, users choose only software firewalls - for the reason that to use them, it is enough to install special software. However, in organizations it is often difficult to find a free computer for a given purpose — besides, it meets all technical requirements, often quite high.
That is why large companies prefer to install specialized software and hardware systems, called the "security appliance". They work most often on the basis of Linux systems or FreeBSD, limited by the functionality to perform a given function.
This solution has the following advantages:
- Easy and simple management: control of the software and hardware complex is carried out from any standard protocol (Telnet, SNMP) - or secure (SSL, SSH).
- High performance: the operation of the operating system is aimed at a single function, it excludes any extraneous services.
- Fault tolerance: software and hardware systems effectively perform their task, the probability of failure is almost impossible.
Firewall Restrictions (Firewall)
The firewall does not filter data that it cannot interpret. The user himself sets up what to do with unrecognized data - in the configuration file, according to which such traffic is processed. Such data packets include traffic from SRTP, IPsec, SSH, TLS protocols, which use cryptography to hide content, protocols that encrypt application-level data (S / MIME and OpenPGP). It is also impossible to filter traffic tunneling if the tunneling mechanism is not understood by the firewall. A significant part of the flaws in firewalls has been fixed in Unified Threat Management UTM systems, sometimes also called NextGen Firewall.
Firewall (firewall, firewall) - These are computer security systems that protect the network from unauthorized access, hackers and various malicious codes. At a time when network security is at the top of the list for computer users, firewalls help ensure the necessary protection and reliability.
What are firewalls really?
These are software or electronic devices that filter traffic flows in unprotected (Internet) and trusted (private or corporate) networks. Firewalls analyze information flows and block those network packets that they consider dangerous (depending on personal firewall settings) for the computer or the entire network.
When connected to the Internet, whether isolated or connected to a local network, computers often become an easy target for malware and hacker attacks. Firewall can provide the level of security that will allow less worry about data protection or loss of access to a computer.
How do they work
Firewalls begin to work every time you connect to the Internet, subjecting all the flow of information to a thorough analysis. Screens can be configured to follow certain “rules”. These rules can be set personally by the user or the network administrator, thereby gaining total control over the flow of incoming and outgoing traffic in your system or networks.
The rules determine who has the right to connect to the Internet, which type of connection can be established, and which files can be downloaded or sent. All traffic can be monitored and monitored by simply setting the protection level and firewall security to maximum.

The benefits of enterprise firewalls
Firewall can be called the "main line of defense" for the network, its protection against unwanted intrusion. Without it, a network that should provide employees with access to important corporate data can open the same access to the information system to anyone. Firewalls cover all known security holes and defenses.
Firewall Logic
Firewalls use 3 types of filtering:
- Packet Filtering or Packet Purity
Data streams consist of information packets and firewalls scan these packets for the presence of dangerous or unwanted (depending on the selected settings).
- Proxy - in this case, the firewalls act as a recipient, and then forward the information to the network node that performed the request. In the same way it works in the opposite direction.
- Inspection - in this case, instead of analyzing each information packet, the firewall monitors and stores the key characteristics of all outgoing requests and checks the incoming information for compliance with the specified parameters.
Types of firewalls
- Software Firewalls - New generation operating systems usually have built-in firewalls, but you can always buy a software firewall separately.
- Hardware Firewalls - These are usually routers with a built-in Ethernet card and a condenser. A computer or computers on a local network are connected to a router and go online.
Firewalls just needed for any computer with access to the global network. They protect against all types of threats and unauthorized access: from trojans, viruses or using your PC's resources for DOS attacks.
Firewalls
When it comes to protection against attacks, the first thing that comes to mind for most users is firewalls. And it is natural. This technology is one of the first and therefore the most famous. So what is a firewall? Generally speaking, it is a tool that separates access between two networks (or, in a particular case, nodes) with different security requirements. In the most common case, a firewall is established between the corporate network and the Internet.
A firewall that protects many (at least two) nodes at once is designed to solve two problems, each of which is important in its own way and, depending on the organization using the firewall, has a higher priority than the other:
- Restriction of access of external (in relation to the protected network) users to internal resources of the corporate network. Such users may include partners, remote users, hackers, and even company employees trying to gain access to the firewall-protected database servers.
Differentiation of access of users of the protected network to external resources. The solution to this problem allows, for example, to regulate access to servers that are not required for the performance of official duties.
All firewalls use one of two mutually exclusive principles in their work:
- "Everything is permitted that is not explicitly prohibited." On the one hand, this principle facilitates the administration of a firewall, since no presetting is required from the administrator - the firewall starts working immediately after switching on the power supply. Any network packet that arrives at the ITU is passed through it, if not prohibited by the rules. On the other hand, in the case of incorrect configuration, this rule makes the firewall a leaky sieve that does not protect against most of the unauthorized actions described in previous chapters. Therefore, manufacturers are currently
firewalls virtually abandoned the use of this principle.
- "Everything is forbidden, not explicitly permitted." This principle makes the firewall almost impregnable wall (if for a while forget about the possibility of undermining this wall, its bypass and penetration through unprotected loopholes). However, as is usually the case, increasing security, we thereby burden the security administrator with additional tasks to pre-configure the firewall rule base. After the inclusion of such an ITU in the network, it becomes unavailable for any kind of traffic. The administrator must set one or more rules for each type of allowed interaction.
Classification
Until now, there is no single and generally accepted classification of firewalls. Each manufacturer chooses a classification that is convenient for itself and aligns it with the firewall developed by this manufacturer. However, based on the ITU’s informal definition above, the following classes can be distinguished, taking into account the OSI layers or the TCP / IP stack:
- switches operating on the data link layer;
- network or packet filters, which, as the name implies, operate at the network level;
- session level gateways (circuit-level proxy);
- application level intermediaries (application proxy or application gateway);
- stateful inspectors.
Switches
These devices operating on the data link layer are not considered to be classified as firewalls, since they differentiate access within the local network and cannot be used to restrict traffic from the Internet. However, based on the fact that the firewall shares access between two networks or nodes, this allocation is quite natural.
Many switch manufacturers, such as Cisco, Nortel, 3Com, allow filtering traffic based on the MAC addresses contained in frames trying to access a specific switch port. This feature is most effectively implemented in Cisco solutions, in particular in the family of Catalyst switches, which have Port Security mechanism. However, it should be noted that almost all modern network cards allow software to change their MAC-addresses, which leads to the inefficiency of this filtering method. Therefore, there are other parameters that can be used as a sign of filtering. For example, VLANs that delimit the traffic between them - the traffic of one VLAN never intersects with the traffic of another VLAN. More "advanced" switches can function not only on the second, but also on the third, fourth (for example, Catalyst) and even the seventh levels of the OSI model (for example, TopLayer AppSwitch). It is necessary to immediately make a small note. There is some confusion in terminology. Some manufacturers mention switching on the fifth level, others - on the seventh. Both are right, but ... For marketing purposes, a switching statement at 7, not 5 levels looks more effective. Although in fact in both cases the same is implied. Indeed, in the TCP / IP model there are only five levels and the last, applied level includes the final three levels that exist in the OSI / ISO model.
Packet filters
Packet filters are one of the first and most common firewalls that operate at the third network level and decide to allow traffic to the network based on the information in the packet header. Many filters can also handle packet headers and higher layers (for example, TCP or UDP). The prevalence of these firewalls is due to the fact that this technology is used in the absolute majority of routers (the so-called screening router, screening router) and even switches (for example, in Cisco solutions). As parameters used in the analysis of network packet headers, can be used:
- addresses of senders and recipients;
- protocol type (TCP, UDP, ICMP, etc.);
- port numbers of senders and receivers (for TCP and UDP traffic);
- other packet header parameters (for example, TCP header flags).
With the help of these parameters described in a special set of rules, you can set a fairly flexible scheme of access control. When a packet arrives at any of the interfaces of the router, it first determines whether it can deliver the packet to its destination (i.e., whether it can perform the routing process). And only then the router checks against the set of rules (the so-called access control list, access control list), checking whether it should route this packet. When creating rules for packet filters, you can use two sources of information: internal and external. The first source includes the already-named network packet header fields. The second, less commonly used source operates with information external to the network packets. For example, the date and time of the network packet.
Network filters, having a number of advantages, are not without some serious drawbacks. First, based on the fact that they analyze only the header (such filters are called stateless packet filtering), the data field, which may contain information contrary to the security policy, remains outside the scope of consideration. For example, this field may contain a command to access the password file via FTP or HTTP, which is a sign of hostile activity. Another example. The packet filter can pass a TCP packet from the node with which no active sessions are currently open to the protected network. Because If the firewall that functions at the network level does not analyze the information inherent in the transport and higher level, it will pass such a packet to the network. In general, the lack of packet filters is that they do not know how to analyze traffic at the application level, where many attacks take place - penetration of viruses, Internet worms, denial of service, etc. Some vendors, such as Cisco, offer stateful packet filtering, which stores information about the state of current sessions, which helps prevent some attacks (such as those described in the last example).
Another drawback of packet filters is the complexity of configuration and administration. You have to create at least two rules for each type of allowed interaction (for incoming and outgoing traffic). Moreover, some rules, for example, implemented in Cisco solutions, are different for each interface of the router, which only complicates the creation of a table of rules (access control list). An uncontrolled increase in the number of rules can lead to gaps in the first line of defense created by packet filters. There are cases when the router rule tables contained thousands of rules. Just imagine what kind of headache administrators would face if they wanted to localize any problem with traffic passing. And do not forget that when setting up a filter, a situation may occur when one rule contradicts the other. The increase in the number of rules brings with it another problem - a decrease in the performance of the firewall. After all, the incoming package is checked for compliance with the table of rules, starting from its top, which in turn requires careful attention to the order of the rules. Such checking is carried out until the corresponding rule is found or the end of the table is reached. In many implementations, each new rule, at least not much, but still reduces the overall performance of the filter. One of the few exceptions is the Cisco product that has been repeatedly mentioned, which implements highly efficient mechanisms for processing network traffic.
Another drawback of packet filters is weak traffic authentication, which is carried out only on the basis of the sender's address. The current version of IP (v4) allows you to easily substitute such an address, substituting for it any one of the addresses belonging to the address space of the IP protocol, thus realizing the IP addressing attack (IP Spoofing). And even if the address of the sending computer has not changed, what prevents the attacker from sitting at this computer. After all, the network filter does not request a user ID and password from the packet, since This information belongs to the application level.
ITU data can be implemented both in hardware, for example, in Cisco filtering routers, and in software, for example, in Windows 2000, Unix, etc. Moreover, the packet filter can be installed not only on the device located on the border between two networks (for example, on the router), but also on the user's workstation, thereby increasing its security.
However, the simplicity of the implementation of packet filters, their high performance and low price (often such filters are freely distributed) outweighs these shortcomings and causes their ubiquitous distribution and use as a mandatory (and often the only) element of the network security system. In addition, they are an integral part of almost all firewalls that use state monitoring and are described below.
| Virtues | disadvantages |
| High speed work. | There is no possibility to analyze the application layer. |
| Ease of implementation. | No protection against address spoofing. |
| This feature is built into all routers and many operating systems, which does not require additional financial costs. | The complexity of configuration and administration. |
| Low cost or free distribution (in case of purchase). | Increasing the number of rules may decrease performance. |
| Requires detailed knowledge of network services and protocols. | |
| No control of the connection status. | |
| The difficulty of functioning in networks with dynamic distribution of addresses. |
Fig. “Batch Filter”
Session Level Gateways
The session-level gateway is another technology used in firewalls, but today it is very difficult to find it in the form of a single technology implemented in a firewall. They are usually supplied as part of application gateways or state inspectors. In addition, the level of protection they provide is slightly higher than that of packet filters, with lower performance.
The meaning of filtering technology at the session level is that the gateway eliminates the direct interaction of the two nodes, acting as a so-called. intermediary (proxy), which intercepts all requests from one node for access to another and, after verifying the validity of such requests, establishes a connection. After that, the session-level gateway simply copies the packets transmitted within one session between two nodes, without performing additional filtering. As soon as an authorized connection is established, the gateway places relevant information in the special connection table (sender and recipient addresses, connection status, sequence number information, etc.). As soon as the communication session is completed, its entry is removed from this table. All subsequent packets that may be generated by an attacker and “as if referring” to an already completed connection are discarded.
The advantage of this technology, of which SOCKS is a prominent representative, is that it excludes direct contact between two nodes. The gateway address of the session level is the only element that links the external network, which is infested by hackers, with internal, protected resources. In addition, since the connection between the nodes is established only after verifying its validity, the gateway thereby prevents the implementation of address spoofing inherent in packet filters.
Despite the apparent effectiveness of this technology, it has one very serious drawback - the inability to verify the content of the data field. Those. thus, the attacker may be able to transfer Trojan horses and other Internet attacks to the protected network. Moreover, the TCP interception capability described in previous chapters (TCP hijacking) allows an attacker, even within the allowed session, to implement his attacks.
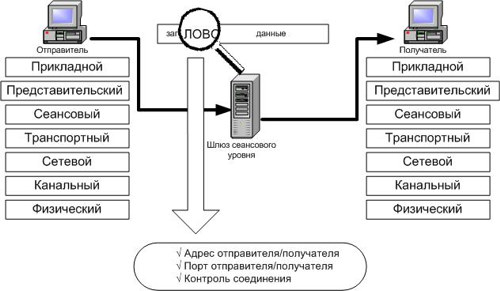
rice "Session Gateway"
Application Level Intermediaries
Application layer mediators are virtually indistinguishable from session-level gateways, with one exception. They also perform an intermediary function between two nodes, excluding their direct interaction, but they allow penetrating the context of the transmitted traffic, since function at the application level. Firewalls built on this technology contain so-called. application proxies, which, “knowing” how an application functions, can process the traffic generated by them. Thus, these intermediaries may, for example, allow the outgoing traffic GET command (receiving file) of the FTP protocol and prohibit the PUT command (send file) and vice versa. Another difference from session level gateways is the ability to filter each packet.
However, as can be seen from the above description, if for any of the applications there is no application broker, then the firewall will not be able to handle the traffic of such an application, and it will be discarded. That is why it is so important that the firewall manufacturer develops intermediaries for new applications in a timely manner, for example, for multimedia applications.
| Virtues | disadvantages |
| Analysis at the application level and the possibility of implementing additional protection mechanisms (for example, content analysis). | The inability to analyze traffic from the "unknown" application. |
| Eliminate direct interaction between two nodes. | Low performance. |
| High level of security. | Vulnerability to attacks at the level of OS and applications. |
| Monitoring connection status. | Requirement to change client software modification. |
| There is not always an intermediary for applications based on UDP and RPC protocols. | |
| Dual analysis - at the application level and intermediary level. |

rice "Application Level Intermediary"
State inspectors
Each of these classes of firewalls has several advantages and can be used to protect corporate networks. However, it would be much more efficient to combine all the mentioned ITU classes in one device. This was done in the state inspectors, which combine all the advantages of the above-mentioned types of screens, starting the analysis of traffic from the network and ending with the application levels, which allows you to combine seemingly incompatible things in one device - greater performance and high security. These firewalls allow you to control:
- each transmitted packet is based on the existing rule table;
- each session - based on the state table;
- each application is based on developed intermediaries.
Acting on the principle of an “advanced” session-level gateway, the state inspector, however, does not prevent the establishment of a connection between two nodes, due to the performance of such a firewall, significantly higher than the session-level and application-level gateways, approaching the values found only in packet filters. Another advantage of stateful firewalls is transparency for the end user, which does not require additional configuration or configuration of client software.
Concluding the description of the firewall classes, we want to note that the term "stateful inspection", introduced by Check Point Software, was so much loved by manufacturers that it is now very difficult to find a firewall that would not fall into this category (even if it does not implement this technology). ). Thus, now there are only two classes of firewalls on the market - state inspectors and packet filters.
Firewall selection
There is a wonderful Russian proverb: "Do not put all your eggs in one basket." It is on this principle that the firewall should be chosen. You can not make a clear choice in favor of any of these screens. It is better if you can use two firewalls, thus building a defense system in your network. If one of the screens is incapacitated, then until that time its performance has been restored, the entire screen will take over the second screen. The combination of "packet filter - state inspector (or application level proxy)" is usually used. And this combination is also good because you don’t have to spend money on purchasing a packet filter already built into the router installed on the edge of your network.
Opportunities
In addition to filtering traffic, firewalls allow you to perform other equally important functions, without which the provision of perimeter protection would be incomplete. Of course, the list below is not exhaustive, but this material is not a guide for choosing a firewall. We just point out some means of protection against the attacks described earlier.
Network Address Translation
As shown earlier, an attacker needs to know the address of his victim in order to implement many attacks. To hide these addresses, as well as the topology of the entire network, firewalls perform a very important function - network address translation (network address translation). Translation can be done in two ways - dynamically and statically. In the first case, the address is allocated to the node at the time of accessing the firewall. After the connection is completed, the address is released and can be used by any other node in the corporate network. In the second case, the node address is always associated with one ITU address.
rice "Network Address Translation"
User Authentication
Firewalls, in addition to allowing or denying admission of various applications to the network, can also perform similar actions for users who wish to access external or internal resources shared by the firewall. At the same time, authentication (authentication) of a user can be performed either by presenting a regular identifier (name) and password, or using more reliable methods, for example, using SecureID or digital certificates.

rice "Authentication"
Event registration
Being a critical element of the corporate network protection system, the firewall has the ability to register all actions recorded by it. Such actions include not only skipping or blocking network packets, but also changing the rules for access control by the security administrator and other actions. Such registration allows you to access the created logs as needed - in the event of a security incident or gathering evidence for submitting them to the courts or for internal investigation.
Implementation
There are two options for the implementation of firewalls - software and software and hardware. The second option can also be implemented in two ways - as a specialized device and as a module in a router or switch. Interest in software and hardware solutions has increased worldwide over the past two years. Such solutions gradually supplant "purely" software systems and begin to play the first violin in this market.
The first solution is the most frequently used and at first glance more attractive. This is due to the fact that, in the opinion of many, for its application it is enough only to purchase firewall software and install it on any computer in the organization. However, in practice, it is far from always that an organization has a free computer, and it also satisfies rather high requirements for system resources. Therefore, simultaneously with the acquisition of software, a computer is also purchased for its installation. Then comes the process of installing an operating system on a computer and setting it up, which also requires time and payment for installers. And only after that the attack detection system software is installed and configured. As you can see, the use of a regular person is not as easy as it seems at first glance. That is why in recent years specialized software and hardware solutions, called the security appliance, have begun to receive. They are supplied as special software and hardware systems using specialized or standard operating systems (usually based on FreeBSD or Linux), "trimmed" to perform only specified functions. The advantages of such solutions include:
- Ease of implementation in information processing technology. Since such devices are already delivered with a pre-installed and configured operating system and protective mechanisms, it is only necessary to connect it to the network, which is performed within a few minutes. And although some adjustment is still required, the time spent on it is significantly less than in the case of installation and configuration of the firewall from scratch.
- Ease of Management. These devices can be controlled from any Windows 9x, NT, 2000 or Unix workstation. The management console communicates with the device using either standard protocols, such as Telnet or SNMP, or using specialized or secure protocols, such as Ssh or SSL.
- Performance. Due to the fact that all "unnecessary" services and subsystems are excluded from the operating system, the device works more efficiently in terms of performance and reliability.
- Fault tolerance and high availability. Implementing a firewall in a special device allows you to implement mechanisms to ensure not only software, but also hardware fault tolerance and high availability. Such devices are relatively easy to cluster.
- Focusing on protection. Solving only network security tasks does not waste resources on other functions, such as routing, etc. Usually, an attempt to create a universal device that solves many problems at once does not lead to anything good.
In a report published by the independent consulting company Gartner Group in June 1997, it was written that by 2002, 80% of companies with revenues from $ 20 million to $ 200 million would choose hardware solutions, not software. The main reason for this choice is to provide the same high level of protection as in software solutions, but for less money. And the second reason is the simplicity and ease of integrating such solutions into the corporate system.
At first glance, such hardware implementations are significantly more expensive, but this is only at first glance. The cost of software and hardware solutions is about $ 5000-12000. The cost of a solution based on the use of software that performs similar functions may be significantly higher. This is despite the fact that the software itself costs less. This effect is achieved due to the fact that the cost of a software solution includes:
- The cost of the computer.
- The cost of a licensed distribution of the operating system.
- Cost of accompanying software (for example, Internet Explorer browser or Oracle DBMS).
- The cost of installation costs and configure the entire complex as a whole. Typically, these costs are 20-30% of the cost of the components of the entire complex.
- The cost of supporting all components of the complex (computer and its hardware components, operating system, additional software, etc.).
For the software and hardware complex of these "additional" costs does not exist, because they are already included in the price of "iron".
However, it should immediately be noted that a specialized computer is not the same as a router with attack detection functions (for example, routers with Cisco Secure Integrated Software). At the router manufacturer, the priority is always to improve the process and increase the speed of routing. And only then he tries to implement the protection features. Therefore, making a choice between routing and protection, they always make it in favor of routing. As practice shows, the use of protective mechanisms on routers significantly reduces their performance. Or the protective functions are limited.
disadvantages
Above we have already listed some of the shortcomings inherent in firewalls, as well as ways to circumvent them. Below we will indicate some more of them.
Restriction of network services functionality
Some corporate networks use topologies that are difficult to “get along” with a firewall (for example, broadcast traffic), or use some services (for example, NFS) in such a way that the application of ITU requires a significant restructuring of the entire network infrastructure. In such a situation, the relative costs of acquiring and configuring the firewall can be comparable to the damage associated with the absence of ITU.
This problem can be solved only by correctly designing the network topology at the initial stage of creating a corporate information system. This will not only reduce the subsequent material costs for the acquisition of information security tools, but also effectively integrate firewalls into the existing information processing technology. If the network is already designed and functioning, then it may be worthwhile to think about using some other solution instead of a firewall, for example, an attack detection system.
Potentially dangerous opportunities
New features that have emerged recently, and which make life easier for Internet users, have been developed with little regard for security requirements. For example, JavaScript, Java, ActiveX and other services focused on working with data. The specificity of mobile code is such that it can be used both as a means for carrying out attacks and as an object of attack. In the first variant, the danger is that the mobile code is downloaded to the user's computer and executed on it as a normal program, gaining access to system resources. The second option, as a rule, is used to modify the mobile code - as a preliminary stage before carrying out attacks on the user's local computer. Attacks on the mobile code, as a means of performing any functions, have not yet become widespread. This is due to the fact that the mobile code has not yet been applied to perform any serious operations, for example, conducting financial transactions. Although there are already known examples of banking systems, including Russian ones, using Java technology to work with a client.
As a means for carrying out attacks, a mobile code can be implemented in the form of:
- a virus that intrudes into the information system and destroys data on local disks, constantly modifying its code, thereby making it difficult to detect and delete;
- an agent intercepting passwords, credit card numbers, etc .;
- a program that copies confidential files containing business and financial information;
- And so on.
Such programs can be masked under animated banners, interactive games, sound files, etc. Russian users do not often use a computer to conduct financial transactions and other actions that could violate the confidentiality of data. Therefore, we consider examples of a hostile mobile code that disrupts the operation of the node on which it runs. This is the easiest to implement and, as a result, a frequently used threat that any Internet user can undergo. Such a threat can be accomplished by:
- creating high-priority processes that perform unauthorized actions;
- generating a large number of windows;
- "capture" a large amount of memory and important system classes;
- CPU load infinite loop;
- etc.
The usual approach used to detect mobile code is to scan all incoming traffic on the 80th or 443th ports used by the HHTP and HTTPS protocols in order to identify elements such as the corresponding tags. But this is not enough to stop the mobile code, because you can get ActiveX controls and Java applets in other ways. For example, imagine that a Java applet (usually having the extension .class) impersonates itself as an image (that is, it has the extension gif or jpg). If the firewall considers that this image, then it is passed to the network and loaded into the browser cache, after which the browser crashes, since the downloaded file is not an image. However, it does not matter - the mobile code is already on the computer. And if later it can be activated, then there may be serious problems with the security of the system. Another method of entry is to use a non-standard port to operate a web server.
One of the security options, for example for Java applets, can be considered a scan of all traffic passing in the protected segment in order to detect the presence of specific code sections. Such detection is performed by searching for the number of the identifying byte-code, which in hexadecimal form looks like "CA FE BA BE". However, this approach is practically not used by security vendors, as traffic is usually too intense to filter its flow through each port to identify specific text fragments.
Viruses and attacks
Virtually no firewall has built-in protection mechanisms against viruses and, in general, from attacks. As a rule, this feature is realized by attaching additional modules or third-party programs to ITU (for example, Trend Micro's IT system for Check Point Firewall-1 or RealSecure attack detection system for it). The use of nonstandard archivers or data transfer formats, as well as traffic encryption, reduces all anti-virus protection to nothing. How can you protect against viruses or attacks if they pass through the firewall in an encrypted form and are decrypted only on the end devices of clients?
In this case, it is better to be safe and prohibit the passage through the firewall data in an unknown format. To control the contents of the encrypted data at the moment nothing can be offered. In this case, it remains to hope that protection against viruses and attacks is carried out on terminal devices. For example, using system agents system RealSecure.
Performance degradation
Very often, firewalls are the bottleneck of the network, reducing its throughput. In those cases when it is necessary to analyze not only the header (as packet filters do), but also the content of each packet ("proxy"), the performance of the firewall is significantly reduced. For networks with heavy traffic, the use of regular firewalls becomes impractical. In such cases, the detection of and response to attacks should be put in the first place, and traffic should be blocked only in the event of an immediate threat. Moreover, some attack detection tools (for example, BlackICE Gigabit Sentry) can function at gigabit speeds.
The trade-off between firewall types is greater flexibility in packet filters versus greater security and excellent controllability in application level gateways or state inspectors. Although at first glance it seems that packet filters should be faster, because they are simpler and only process packet headers without affecting their contents, this is not always true. Many firewalls built on an application gateway show higher speeds than routers and are the best choice for access control. This is due to the fact that, as already mentioned, routers are non-specialized devices and filtering functions for them are not priority.
Personal Firewalls
Over the past few years, major changes have occurred in the structure of corporate networks. If before the boundaries of such networks could be clearly delineated, now it is almost impossible. Not long ago, such a border passed through all routers or other devices (for example, modems) through which access to external networks was made. In remote offices of the organization, the situation was similar. However, now the full-fledged user of the network protected by a firewall is an employee who is outside the protected perimeter. Such employees include users who work at home or are on a business trip. Do they need protection? Sure. But all traditional firewalls are built in such a way that protected users and resources must be under the protection of their protection, i.e. from the inside, which is impossible for mobile users. In order to eliminate this problem, two approaches were proposed - virtual private networks (VPN), which will be described later, and distributed firewalls (distributed firewalls). An example of the first solution is Check Point Software's VPN-1 (http://www.checkpoint.com). Such a scheme, similar to the octopus that had spread its tentacles, had only one drawback - the remote site itself was subject to attacks, although access to the corporate network was protected from unauthorized impacts. A Trojan horse installed on a remote workstation could have enabled an intruder to penetrate through the firewall and through a secure channel. After all, VPN encrypts both normal and unauthorized traffic, making no distinction between them. It was then that the idea of a distributed firewall was born, which would be a mini-screen protecting not the entire network, but only a single computer. Examples of such a solution are the BlackICE Agent of Internet Security Systems (http://www.iss.net) or RealSecure Server Sensor from the same manufacturer. This solution was also liked by home users, who finally got the opportunity to protect their computers from intruders scouring the network. But, since many functions of distributed ITU (for example, centralized management or distribution of security policies) for home users were superfluous, then the technology of distributed ITU was modified and the new approach was called the “personal firewall” (personal firewall), bright representatives of which are ZoneAlarm and BlackICE Defender companies ZoneLabs (http://www.zonelabs.com) and ISS respectively. Check Point Software has come to the fore and here by offering a VPN-1 SecureClient and VPN-1 SecureServer solution, which not only protects the computers on which they are installed from external attacks, but also protects the traffic transmitted outside this node (i.e. by organizing client \\ server vpn). It was this decision that made the network subject to firewalls with vaguely defined boundaries.
What is the difference between a personal firewall and a distributed firewall? The main difference is the presence of a centralized management function. If personal firewalls are managed only from the computer on which they are installed, and are ideal for home use, then distributed firewalls can be managed centrally from a single management console installed in the main office of the organization. Such differences allowed some manufacturers to release their solutions in two versions - personal (for home users) and distributed (for corporate users). So, for example, came Internet Security Systems, which offers a BlackICE Defender personal firewall and a BlackICE Agent distributed firewall.
What functions should an effective personal ITU have? Firstly, this screen should not be a passive program, which only does what blocks incoming traffic to a computer by specified criteria, which usually include the address and port of the source. Malefactors learned long ago to bypass such simple protective mechanisms and on the Internet you can find a large number of programs that can penetrate many traditional protective barriers. An example of such a program is the Trojan horse SubSeven 2.2, which allows you to perform a large number of functions on a compromised computer without the knowledge of its owner. To defend oneself, a tool is needed that will allow for a deeper analysis of each network packet aimed at the protected node. Such a tool is an attack detection system that detects traces of hacking activity in traffic passed through the firewall. She does not blindly trust such permits as the source address and port. As is well known, the IP protocol, on the basis of which the modern Internet is built, does not have any serious security mechanisms, which makes it easy to replace your real address, thus making it impossible to track an intruder. Moreover, a hacker can "substitute" someone else, replacing your address with the address of a surrogate. And finally, for some attacks (for example, “denial of service”) the source address is not needed at all and according to statistics in 95% of cases this address is changed by the hacker. There is a good analogy. A personal firewall is a security guard in a building who issues passes to all visitors. In such a situation, an attacker can easily carry a weapon or a bomb into a building. However, if you put a metal detector at the entrance, the situation changes radically and it is no longer easy for an attacker to carry prohibited items into the protected area.
Unfortunately, it is necessary to note that few firewalls have a built-in attack detection system. One such solution is the BlackICE Defender and BlackICE Agent systems of Internet Security Systems. Any of the components of the BlackICE family contains two main modules that detect and block unauthorized activities - BlackICE Firewall and BlackICE IDS. BlackICE Firewall is responsible for blocking network traffic from certain IP addresses and TCP / UDP ports. Pre-blocking traffic by certain criteria allows you to increase system performance by reducing the number of "unnecessary" operations to process unauthorized traffic. This component can be configured both manually and automatically. In the latter case, reconfiguration occurs after the detection of unauthorized activities by the BlackICE IDS module. In this case, blocking traffic can be carried out for any period of time. BlackICE Firewall works directly with the network card, bypassing the protocol stack built into the operating system, which eliminates the danger of using many known vulnerabilities associated with incorrect implementation of the stack in the OS. BlackICE IDS is responsible for detecting attacks and other traces of unauthorized activity in the traffic coming from the BlackICE Firewall module, and uses a patented seven-level protocol analysis algorithm.
The next mechanism that an effective personal firewall should have is protection against dangerous content that can be obtained from the Internet. This content includes Java applets and ActiveX controls, ShockWave code, and JavaScript, Jscript, and VBScript scripts. With the help of these, on the one hand, irreplaceable and convenient technologies, a large number of unauthorized actions can be performed on a computer. Starting from the introduction of viruses and the installation of Trojan horses and ending with the theft or removal of all information. Also, personal firewalls should protect against cookies, which can reveal confidential information about the owner of the computer.
Some personal ITUs (for example, Norton Internet Security from Symantec) have built in anti-virus systems that, in addition to detecting Trojans, can detect a large number of viruses, including macro viruses and Internet worms. Often, manufacturers embed VPN modules in their products (for example, PGP Desktop Security or VPN-1 SecureClient), which are responsible for ensuring secure interaction with the central office.
Because distributed screens are managed centrally, they must have an effective configuration, administration and control mechanism that allows the security administrator to obtain detailed information about the recorded attempts to penetrate the protected nodes without additional efforts. Moreover, in some cases, it is necessary to initiate a computer crime investigation procedure or gather evidence to go to law enforcement agencies. And there will be an indispensable mechanism for tracking an attacker (back tracing), implemented in some firewalls. For example, the already mentioned BlackICE Agent and Defender, allow you to track an attacker carrying out an attack on a protected computer, and collect the following information about a hacker:
- IP-, DNS-, WINS-, NetBIOS- and MAC-addresses of the computer from which the attack is carried out.
- The name under which the attacker entered the network.
Equally important is the ability to remotely update the personal firewall software (for example, in VPN-1 SecureClient). Otherwise, the administrator would have to independently visit each of the computer owners and update its security software. Imagine what kind of disturbance this would have caused the owners of computers, which they would tear off from their work. The remote and, most importantly, imperceptible for the owner of the computer, the update (including updating the signatures of attacks and viruses) removes this problem and eases the hard work of the security administrator. When implementing remote control, you should not forget about the protection of traffic transmitted between the central console and remote agents. An attacker could intercept or replace these commands, which would violate the security of remote sites.
In conclusion of this section I want to say that the correct choice of a personal or distributed firewall will increase the security of computers, which under normal conditions remain unprotected and can serve as a point of entry into the corporate network.
11. Firewalls and their role in building secure systems
Firewall or network screen ?? a set of hardware or software that monitors and filters network packets passing through it in accordance with specified rules.
The main task of the firewall is to protect computer networks or individual nodes from unauthorized access. Also, firewalls are often called filters, as their main task ?? do not pass (filter) packets that do not match the criteria defined in the configuration.
Some firewalls also allow address translation ?? dynamic replacement of intranet (gray) addresses or ports with external ones used outside the LAN.
Other names
Firewall (it. Brandmauer) ?? borrowed from the German language, the term is an analogue of the English firewall in its original meaning (the wall that separates adjacent buildings, preventing the spread of fire). Interestingly, in the field of computer technology in German, the word "Firewall" is used.
Firewall, firewall, firewall, firewall ?? formed by transliterating the English term firewall.
Varieties of firewalls
Firewalls are classified into different types depending on the following characteristics:
- whether the screen provides a connection between one node and the network or between two or more different networks;
- at the level of what network protocols the data flow is controlled;
- whether active connections are monitored or not.
Depending on the coverage of the monitored data streams, firewalls are divided into:
- traditional network (or firewall) ?? a program (or an integral part of the operating system) on the gateway (the server transmitting traffic between networks) or a hardware solution controlling incoming and outgoing data flows between connected networks.
- personal firewall ?? the program installed on the user's computer and designed to protect against the unauthorized access of only this computer.
Degenerate case ?? use of traditional firewall server to limit access to its own resources.
Depending on the level at which access control occurs, there is a division into firewalls running on:
- network level when filtering occurs based on the sender and receiver addresses of packets, the transport-level port numbers of the OSI model and static rules set by the administrator;
- session level (also known as stateful) ?? tracking sessions between applications that do not allow packets that violate the TCP / IP specifications often used in malicious operations ?? scanning resources, hacking through incorrect implementations of TCP / IP, disconnection / deceleration of connections, data injection.
- application level, filtering based on the analysis of application data transmitted within the packet. These types of screens allow you to block the transfer of unwanted and potentially dangerous information based on policies and settings.
Some solutions related to application-level firewalls are proxy servers with some firewall features, implementing transparent proxy servers with a specialization in protocols. The capabilities of the proxy server and multiprotocol specialization make filtering much more flexible than on classic firewalls, but such applications have all the disadvantages of proxy servers (for example, traffic anonymization).
Depending on the tracking of active connections, firewalls are:
- stateless (simple filtering), which do not track current connections (for example, TCP), but filter the data stream solely on the basis of static rules;
- stateful stateful packet inspection (SPI) (context-based filtering), with tracking of current connections and skipping only those packets that satisfy the logic and algorithms of the respective protocols and applications. Such types of firewalls make it possible to more effectively deal with various types of DoS attacks and vulnerabilities of some network protocols. In addition, they provide for the functioning of such protocols as H.323, SIP, FTP, etc., which use complex data transfer schemes between recipients, which are difficult to describe by static rules, and often incompatible with standard, stateless network screens.
Typical features
- filtering access to obviously unprotected services;
- preventing the receipt of sensitive information from a protected subnetwork, as well as the introduction of false data into a protected subnetwork using vulnerable services;
- access control to network nodes;
- can register all access attempts both from the outside and from the internal network, which allows keeping records of the use of Internet access by individual network nodes;
- regulation of access to the network;
- notification of suspicious activity, attempts to probe or attack network nodes or the screen itself;
Due to security restrictions, some of the necessary user services may be blocked, such as Telnet, FTP, SMB, NFS, and so on. Therefore, setting up a firewall requires the participation of a network security specialist. Otherwise, the harm from misconfiguration may exceed the benefit.
It should also be noted that the use of firewall increases response time and reduces throughput, since filtering does not occur instantaneously.
Problems not solved by firewall
The firewall itself is not a panacea for all network threats. In particular, he:
- does not protect network nodes from penetrating through “hatches” (English back doors) or software vulnerabilities;
- does not provide protection against many internal threats in the first place ?? data leaks;
- does not protect users from downloading malicious programs, including viruses;
To solve the last two problems, appropriate additional tools are used, in particular, antiviruses. Usually they connect to the firewall and pass the corresponding part of the network traffic through themselves, working as transparent for other network proxies, or receive a copy of all the data sent from the firewall. However, such an analysis requires significant hardware resources, so it is usually carried out on each node of the network independently.
Firewalls (firewall, firewall) make it possible to filter incoming and outgoing traffic through your system. The firewall uses one or more sets of “rules” to inspect network packets as they enter or exit through a network connection, it either allows traffic to pass through or blocks it. Firewall rules can check one or more packet characteristics, including but not limited to the type of protocol, the source or destination host address, and the source or destination port.
Firewalls can seriously increase the security level of a host or network. They can be used to perform one or more of the following tasks:
- To protect and isolate applications, services and machines on the internal network from unwanted traffic coming from the external Internet.
- To restrict or prohibit the access of the internal network hosts to the external Internet services.
- To support network address translation (NAT), which makes it possible to use private IP addresses on the internal network and share one Internet connection (either through one dedicated IP address or via an address from a pool of automatically assigned public addresses).
Firewall Principles
There are two main ways to create firewall rule sets: "including" and "" excluding "." An exclusive firewall allows all traffic to pass, with the exception of traffic matching a set of rules. The enabling firewall acts in exactly the opposite way. It only allows traffic that conforms to the rules and blocks everything else.
An inclusive firewall provides a much greater degree of control over outgoing traffic. Therefore, an inclusive firewall is the best choice for systems that provide services on the Internet. It also controls the type of traffic spawned out and heading to your private network. Traffic that does not fall into the rules is blocked, and the corresponding entries are made in the log file. Inclusive firewalls are usually safer than exclusive firewalls, since they significantly reduce the risk of firewall passing unwanted traffic.
Comment: Unless otherwise indicated, all examples of rule sets and configurations in this section are of the type of inclusive firewall.
Security can be further enhanced using a "" firewall while maintaining the state "". Such a firewall stores information about open connections and allows only traffic through open connections or opening new connections. The lack of stateful firewall is that it can be vulnerable to Denial of Service (DoS) denial of service attacks if many new connections open very quickly. Most firewalls allow you to combine behavior with stateless and stateless, which allows you to create the optimal configuration for each particular system.
What is a firewall
A firewall (other names firewall, firewall) is a protective barrier between your computer and the network to which it is connected. When you go online, your computer becomes visible to the outside world. You are visible through something called a port. A port is a system resource identified by a specific number, allocated to an application that runs on a network host (computer or other network device), to communicate with applications that run on other network hosts (including other applications on the same host). There are many thousands of such ports and, as mentioned above, each has its own unique number.
The most commonly used ports on the world wide web are:
- 80 ?? port for loading web pages;
- 110 ?? used by default for email downloads;
- 25 ?? used by default to send email.
The essence of the firewall is to close ports that you do not use. Otherwise, an attacker or a malicious program (virus, trojan) can penetrate your PC through them. If you are connected to the Internet, then you simply must have a firewall.
What can happen if you don't use a firewall?
If, after installing the operating system, you do not activate the firewall or if it is not activated by default, then your system may be attacked a few minutes after accessing the Internet. Viruses, Trojan worms and spyware can penetrate open ports and cause you a lot of trouble in the future, and you won’t even guess about it. Once, the authoritative edition of PC Format abroad launched an experiment and as a result, the operating system on their completely unprotected computer was rendered completely unsuitable after two and a half hours of surfing the Internet. A firewall could stop some of the attacks that the computer was subjected to.
It is also not necessary to assume that having only a firewall will help protect you from all evils. Do not forget to install the antivirus and then regularly update the databases, as well as regularly download and install security updates for your Windows.
How a firewall helps protect your PC
Most firewalls, including those built into Windows, will alert you about suspicious incoming traffic. But a good firewall should alert you to suspicious outgoing traffic. For example, the built-in Windows XP firewall does not know how to do this, so it’s better to replace it with a third-party program. The presence of suspicious outgoing traffic will help you understand that yourthe computer is already infected Trojan or spyware.

Types of firewalls
Firewalls can be divided into two simple categories: hardware and software. A hardware firewall can be a router that is between your PC and the Internet. In this case, several computers can be connected to it and all of them will be protected by a firewall, which is part of the router. Software firewall ?? This is specialized software that the user installs on his computer.
Even if you already haverouter With a built-in firewall, you can also install a software firewall on each computer individually. Then the attacker will be much harder to penetrate your system.
I hope I could clearly explain what a firewall is and those who still do not use it will begin to do it.
Do not forget to leave a comment. See you again!
Firewall or firewall (in his brandmauer, in English. in Russian border of fire) is a system or a combination of systems that allow you to divide a network into two or more parts and implement a set of rules determining the conditions for passing packets from one part to another (see Figure 1). Most often, this boundary is drawn between local area network businesses and INTERNET, although it can be carried out within the local network of the enterprise. The firewall, thus, passes through all the traffic. For each passing packet, the firewall decides to skip it or discard it. In order for the firewall to make these decisions, it needs to define a set of rules. How these rules are described and what parameters are used in their description will be discussed later.
fig.1
As a rule, firewalls operate on any UNIX platform — most often BSDI, SunOS, AIX, IRIX, etc., less often DOS, VMS, WNT, Windows NT. From hardware platforms, there are INTEL, Sun SPARC, RS6000, Alpha, HP PA-RISC, RISC R4400-R5000 family of processors. In addition to Ethernet, many firewalls support FDDI, Token Ring, 100Base-T, 100VG-AnyLan, various serial devices. Requirements for RAM and hard disk capacity depend on the number of machines in the protected network segment.
Usually, the operating system under which the firewall is running changes is made, the purpose of which is to increase the protection of the firewall itself. These changes affect both the OS kernel and the corresponding configuration files. On the firewall itself, it is not allowed to have user accounts (and therefore potential holes), only an administrator account. Some firewalls work only in single user mode. Many firewalls have a system for checking the integrity of software codes. At the same time, the checksums of the program codes are stored in a protected place and are compared at the start of the program in order to avoid the substitution of software.
All firewalls can be divided into three types:
All types can simultaneously meet in the same firewall. Packet filters
Packet filter firewalls decide whether to drop a packet or discard it by looking at the IP addresses, flags, or TCP port numbers in the header of this packet. The IP address and port number is the information of the network and transport levels, respectively, but the packet filters use the application level information, since All standard TCP / IP services are associated with a specific port number.
To describe the rules for passing a packet, type tables are created:
The field "action" can take values to skip or discard.
The type of packet is TCP, UDP or ICMP.
Flags - Flags from the IP packet header.
The fields "source port" and "destination port" make sense only for TCP and UDP packets. Application Server
Firewalls with application servers use servers specific of services (proxy server) - TELNET, FTP, etc., run on the firewall and pass through all the traffic related to this service. Thus, two connections form between the client and the server: from the client to the firewall and from the firewall to the destination.
The full set of supported servers is different for each specific firewall, but most often there are servers for the following services:
- terminals (Telnet, Rlogin);
- file transfer (ftp);
- email (SMTP, POP3);
- WWW (HTTP);
- Gopher;
- Wais;
- X Window System (X11);
- network printing (LP);
- remote task execution (Rsh);
- Finger;
- usenet news (NNTP);
- Whois;
- RealAudio.
Using application-level servers allows you to solve an important task - to hide the structure of the local network from external users, including information in the headers of mail packets or Domain Name Service (DNS). Another positive feature is the ability to authenticate at the user level (recall that authentication is the process of confirming the identity of something; in this case, it is the process of confirming whether the user really is who he claims to be).
- When describing access rules, parameters are used such as
- service name,
- username,
- allowable time range for using the service,
- computers from which you can use the service
- authentication schemes.
Application-level servers provide the highest level of protection, since interaction with external worlds is realized through a small number of application programs that fully control all incoming and outgoing traffic. Connection level servers
Connection level server is a TCP connection translator. The user forms a connection with a specific port on the firewall, after which the latter makes a connection with the destination on the other side of the firewall. During a session, this translator copies bytes in both directions, acting as a wire.
As a rule, the destination is set in advance, while there may be many sources (one type connection - many). Using different ports, you can create different configurations.
This type of server allows you to create a translator for any user-defined service based on TCP, control access to this service, and collect statistics on its use.
Comparative characteristics of packet filters and application servers
Below are the main advantages and disadvantages of packet filters and application-level servers relative to each other.
- Advantages of packet filters:
- relatively low cost;
- flexibility in defining filtering rules;
- slight delay in passing packets.
- Disadvantages of packet filters:
- the local network is visible (routed) from the INTERNET;
- packet filtering rules are difficult to describe; very good knowledge of TCP and UDP technologies is required;
- if the firewall malfunctions, all the computers behind it become completely unprotected or inaccessible;
- authentication using an IP address can be fooled by using IP spoofing (the attacking system impersonating another one using its IP address);
- no user level authentication.
- Advantages of application level servers:
- local network is invisible from the INTERNET;
- when a firewall malfunctions, packets no longer pass through the firewall, thus there is no threat to the machines protected by it;
- protection at the application level allows a large number of additional checks, thereby reducing the likelihood of hacking using holes in the software;
- user-level authentication can be implemented a system of immediate warning of a hacking attempt.
- Disadvantages of application servers:
- higher than for packet filters;
- the inability to use the RPC and UDP protocols;
- performance is lower than for packet filters.
Virtual networks
A number of firewalls also allow you to organize virtual corporate networks ( Virtual Private Network), i.e. merge several local networks included in the INTERNET into one virtual network. VPN allow you to organize a transparent for users connection of local networks, while maintaining the privacy and integrity of the transmitted information using encryption. In this case, when transmitting via the INTERNET, not only the user's data is encrypted, but also the network information — network addresses, port numbers, etc.
Firewall Connection Diagrams
Different schemes are used to connect firewalls. A firewall can be used as an external router, using supported device types to connect to an external network (see Figure 1). Sometimes the scheme shown in Figure 2 is used, but it should be used only as a last resort, since very careful setup of routers is required and small errors can form serious security holes. 
fig.2
Most often, the connection is made through an external router that supports two Ethernet interfaces (the so-called dual-homed firewall) (two network cards in one computer) (see Figure 3). 
fig.3
At the same time between the external router and the firewall there is only one path that all traffic goes through. Usually the router is configured in such a way that the firewall is the only machine visible from the outside. This scheme is the most preferable in terms of security and reliability of protection.
Another scheme is shown in Fig.4. 
fig.4
In this case, the firewall protects only one subnet of several coming out of the router. In an area that is not protected by a firewall, there are often servers that must be visible from the outside (WWW, FTP, etc.). Most firewalls allow you to place these servers on yourself - a solution that is far from the best in terms of machine load and security of the firewall itself.
There are solutions (see Figure 5) that allow you to organize for servers, which must be visible outside, a third network; this allows you to control access to them, while at the same time maintaining the necessary level of protection of machines in the main network. 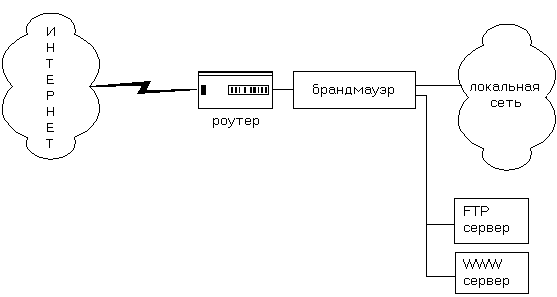
fig.5
At the same time, a lot of attention is paid to the fact that users of the internal network cannot accidentally or intentionally open a hole in the local network through these servers. To increase the level of security, it is possible to use several firewalls in the same network, one after another.
Administration
Ease of administration is one of the key aspects in creating an effective and reliable security system. Errors in defining access rules can form a hole through which a system can be hacked. Therefore, in most firewalls, service utilities are implemented that facilitate entry, deletion, and viewing of a set of rules. The presence of these utilities also makes it possible to check for syntax or logical errors when entering or editing rules. As a rule, these utilities allow you to view information grouped by any criteria, for example, everything related to a specific user or service.
Statistics collection systems and attack warnings
Another important component of the firewall is the statistics and attack warning system. Information about all events - failures, incoming, outgoing connections, number of bytes transferred, services used, connection time, etc. - accumulates in the statistics files. Many firewalls allow you to flexibly define events to be logged, to describe the actions of the firewall during attacks or unauthorized access attempts - this can be a message to the console, a mail message to the system administrator, etc. Immediately displaying a message about a hacking attempt on the console screen or an administrator can help if the attempt was successful and the attacker has already entered the system. Many firewalls include report generators for processing statistics. They allow you to collect statistics on the use of resources by specific users, on the use of services, failures, sources from which unauthorized access attempts were made, etc.
Authentication
Authentication is one of the most important components of firewalls. Before the user is granted the right to use this or that service, it is necessary to make sure that he is really the one for whom he claims to be.
As a rule, the principle called “what he knows” is used - i.e. the user knows some secret word that he sends to the authentication server in response to his request.
One of the authentication schemes is the use of standard UNIX passwords. This scheme is the most vulnerable from the point of view of security - the password can be intercepted and used by another person.
Firewall Security Classes
With regard to the processing of confidential information, automated systems (AS) are divided into three groups:
- Multiuser speakers processing information at various levels of privacy.
- Multi-user speakers, in which all users have equal access to all processed information located on media of different levels of confidentiality.
- Single-user speakers in which the user has access to all the processed information located on media of different confidentiality levels.
In the first group, there are 5 classes of security of the AU: 1A, 1B, 1B, 1G, 1D, in the second and third groups - 2 classes of security: 2A, 2B and 3A, 3B respectively. Class A corresponds to the maximum, class D - the minimum security of the AU.
Firewalls allow you to maintain the security of objects in the internal area, ignoring unauthorized requests from the external area, i.e. carry out screening. As a result, the vulnerability of internal objects is reduced, since the original third-party intruder must overcome the firewall, where the defense mechanisms are configured particularly carefully and tightly. In addition, the screening system, in contrast to the universal one, is more simple and, therefore, safer. It contains only those components that are necessary to perform the shielding functions. Shielding also provides the ability to control information flows directed to the external area, which helps to maintain confidentiality in the internal area. In addition to access control functions, firewalls register information flows.
By the level of security, firewalls are divided into 5 classes. The lowest security class is the fifth. It is used for safe interaction of AC Class 1D with the environment, the fourth - for 1G, the third - for 1B, the second - for 1B, the highest - the first - for 1A.
For Class 2B, 3B speakers, firewalls of at least fifth grade are used.
For class 2A, 3A speakers, depending on the importance of the information being processed, firewalls of the following classes are used:
- when processing information classified as secret - not lower than the third class;
- when processing information with the “top secret” stamp - not lower than the second class;
- when processing information with the stamp of "special importance" - only the first class.
Security indicators are summarized in table 1.
Legend:
| Security Indicators | Security classes | ||||
| 5 | 4 | 3 | 2 | 1 | |
| Access control (data filtering and address translation) | + | + | + | + | = |
| Identification and Authentication | - | - | + | = | + |
| check in | - | + | + | + | = |
| Administration: Identification and Authentication | + | = | + | + | + |
| Administration: Registration | + | + | + | = | = |
| Administration: ease of use | - | - | + | = | + |
| Integrity | + | = | + | + | + |
| Recovery | + | = | = | + | = |
| Testing | + | + | + | + | + |
| Security Administrator's Guide | + | = | = | = | = |
| Test documentation | + | + | + | + | + |
| Design (project) documentation | + | = | + | = | + |
Firewall Guide
The research unit of TruSecure, the ICSA laboratory, developed the “Firewall Buyers Guide” document. In one of the sections of this document the following form of evaluation of the buyer is given:
- Contact information - address and responsible persons.
- Business work environment:
- the number and location of individual institutions (buildings) of the enterprise;
- indication of subdivisions and information of limited nature and information for which the availability of data is important for interaction between the subdivisions, their distribution;
- The indication of external partners with whom it is necessary to organize interaction;
- description of publicly open services;
- requirements for the organization of remote access to the internal information space of the enterprise;
- electronic services using public communication channels (for example, electronic commerce).
- Planned changes in the business environment for the listed parameters.
- Informational environment:
- the number of user workstations with indication of hardware, system and application software;
- network structure with indication of topology, data transmission medium, devices used and protocols;
- the structure of remote access with an indication of the devices used, as well as authentication methods;
- the number of servers with indication of hardware, system and application software;
- the existing system of supporting information systems by suppliers with their indication and boundaries of the field of activity;
- anti-virus systems and other software control systems;
- network and information management technology;
- authentication technologies - list and description.
- Planned changes in the information environment on the listed parameters.
- Internet connection:
- type of internet connection;
- existing firewalls (if any);
- Means of communication with the external environment, used by internal systems;
- internal systems and services accessible from outside;
- e-commerce and other transaction systems;
- an indication of the existence of an approved security policy for access and use of the Internet.
- Planned events (for which a firewall is purchased):
- changes in Internet access methods and enterprise security policies;
- the emergence of new protocols, which must be maintained separately for internal users, users with remote access or special users who are publicly available.
- Required firewall functionality:
- access control;
- messages displayed;
- authentication;
- configuration management;
- control the content of passing traffic;
- registration logs;
- recognition of attacks;
- network options (number of interfaces, access method);
- remote administration;
- system requirements (turnkey, integration with other products, etc.).
- Other conditions:
- the estimated cost of the firewall (how much the company can spend);
- estimated date of commencement of the product;
- requirements for product certificates;
- requirements for the intended administrator of the product and support service;
- special conditions of the contract (if any);
- other comments that are not included in this form.
It is assumed that the company, filling out this form and sending it to the manufacturer, will allow the latter to form the best quality offer for the buyer. Filling out this form, however, and without sending it to anyone, will allow the organization to better understand what solution it needs.